SECURE
DATA LOSS PREVENTION
SECURE.
Our flagship module of the product suite, Secure locks down the employee to make sure company data is safe. With Secure policies in place, the software can prevent data leaking from the four (4) major leak points; Removable drives, Web uploads including cloud storage solutions like DropBox, Email attachments and even printed documents. Also, policies can be set to prevent data from the source location whether it is a file share on the network or an actual application.
CAPTURE & MONITOR USER BEHAVIOR.
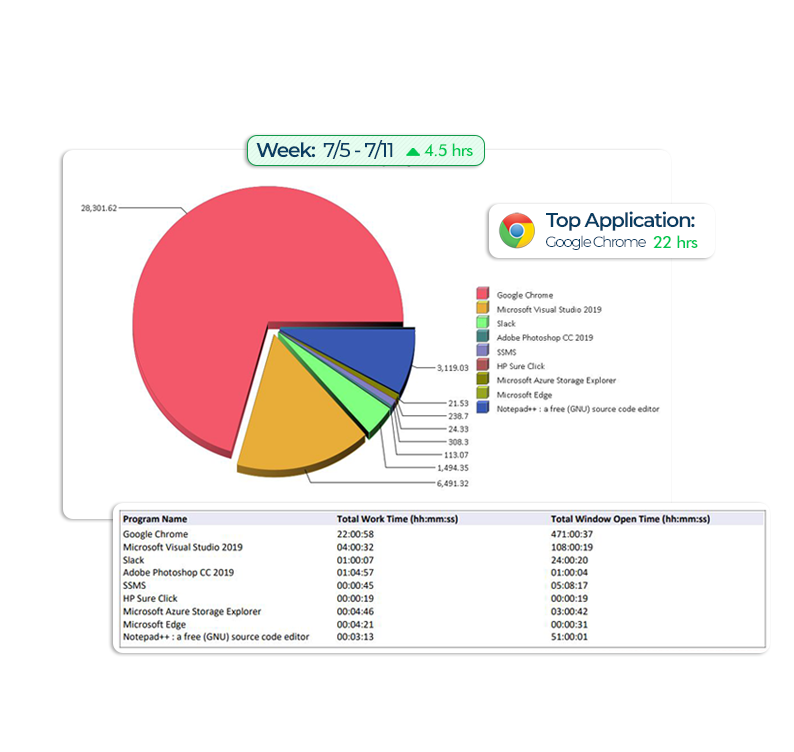
Security and data loss prevention should start with understanding how users use their computers. Who has access to what data, How they use that data, and where they send that data. Pairing Intelligence (Link this to the product page) with Secure allows you to know now what you need to know!

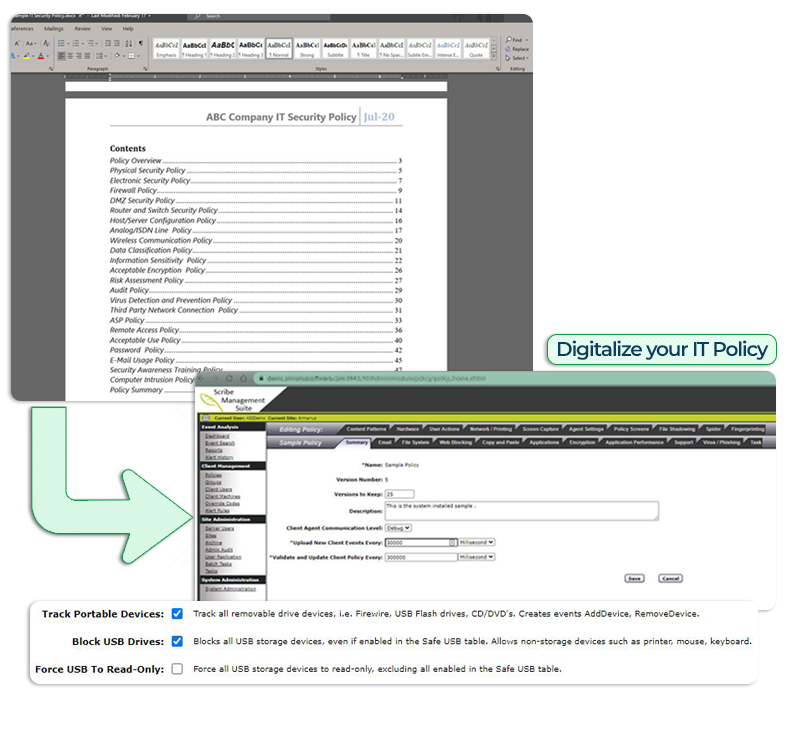
ANALYZE CURRENT IT SECURITY POLICIES.

The first step in any organization should be to review your current data loss prevention policies that your employees have been adhering to. Once you understand what you have and what you can do. Adjust. Adjust your policies to the needs of the business.
IMPLEMENT POLICY
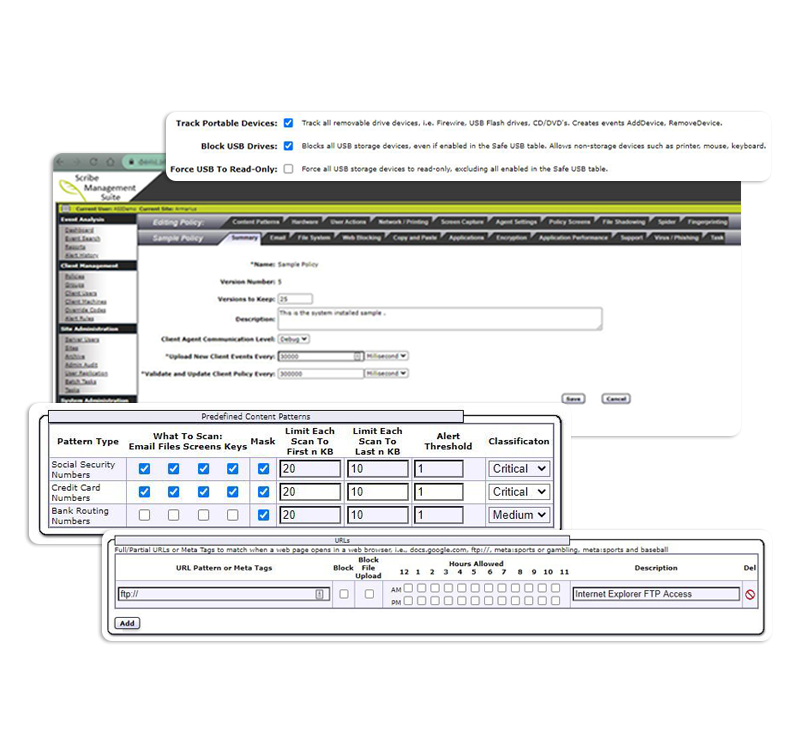
Once you have a good foundation on what the business needs to do. It is best to start implementing those policy changes. From the four major leak points to protecting data at the source.

Policy Options
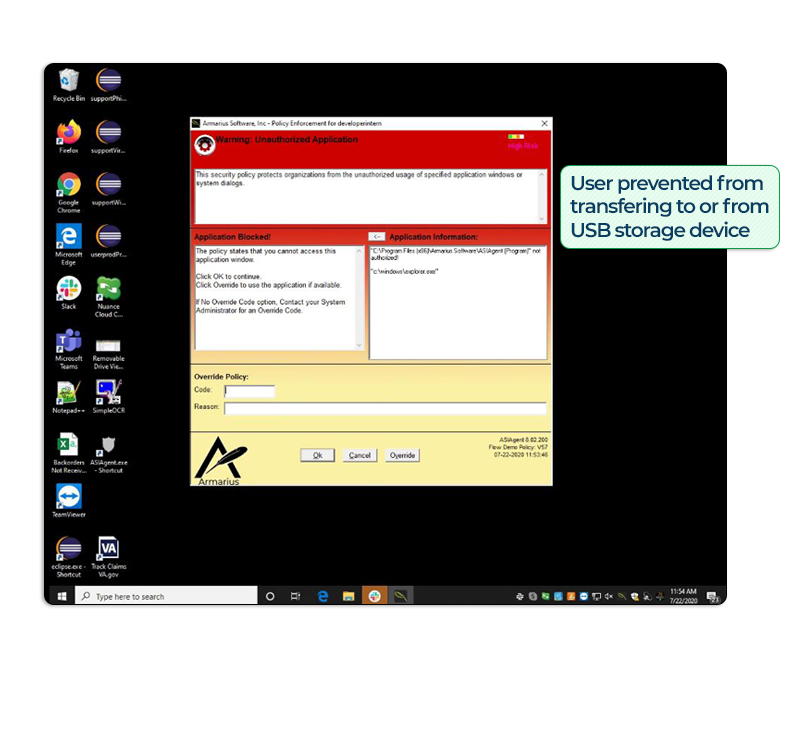
TAKE CONTROL – FEEL SAFE!

Once you have the policies set, you can feel safe and protected.
Testimonials:
“We’ve used the software for it’s ability to electronically enforce our IT security policies. The auditors and examiners are impressed and always have positive things to say about the system once we show them what it does.”
– Security Bank
“Understanding user behavior at the desktop made securing the network and data loss prevention that much easier!”
– American Midwest Bank
“We were pleasantly surprised to discover that many of the software solutions for security we were looking at or had deployed on an individual basis were all included in their comprehensive security solution. There’s a lot of functionality for the cost.”
– Motorola Credit Union


